- Home
- AI & Machine Learning
- Penetration Testing MVPs Before Pilot Launch: How to Avoid Costly Security Mistakes

Penetration Testing MVPs Before Pilot Launch: How to Avoid Costly Security Mistakes
Most startups rush to launch their MVPs. They want users. They want feedback. They want to prove their idea works. But too many skip one critical step: penetration testing. And when they do, they pay for it - hard.
Imagine this: your app launches. Users sign up. Everything looks great. Then, one morning, you get an email from a stranger saying they’ve accessed your entire customer database. Not because of a hack. Because your admin API was exposed. No password. No authentication. Just sitting there, wide open. That’s not a hypothetical. That’s what happened to a healthtech startup in Austin last year. They skipped penetration testing to hit their launch date. The cost? $87,000 in remediation, legal fees, and lost trust. And that’s the lucky ones. Others never recover.
Here’s the truth: your MVP isn’t too early to test for security. It’s too early to ignore it. The cheapest time to fix a vulnerability is before you even let a single user in. According to the Ponemon Institute, fixing a flaw during MVP development costs about $1,200. Wait until after launch? That jumps to $15,400. That’s over 12 times more expensive. And it’s not just money. It’s your reputation. Your funding. Your future.
Why Penetration Testing Isn’t Just for Big Companies
You might think penetration testing is for banks and Fortune 500s. Not for a team of three building a SaaS tool in a garage. But that’s exactly when you need it most. Startups are low-hanging fruit. Attackers know you’re moving fast. They know you’re focused on features, not firewalls. And they’re right to target you.
According to CISA’s 2023 report, startups that run pre-launch penetration tests see 63% fewer critical security incidents in their first year. That’s not luck. That’s strategy. And it’s not about being perfect. It’s about being smarter than the attacker. You don’t need to lock down every door. You just need to make sure the ones that matter are closed.
Most MVPs fail for the same reason: they’re built without thinking about how someone might break them. A login form that doesn’t limit retries. An API endpoint that returns all user data with a single call. A database backup file left in the public folder. These aren’t complex issues. They’re simple mistakes. And penetration testing finds them before your users do.
What Kind of Testing Works Best for MVPs?
Not all penetration testing is the same. There are three main types: black box, white box, and gray box.
- Black box means testers know nothing about your system. They’re like strangers trying to break in. This mimics real-world attackers, but it’s slow and misses internal flaws.
- White box gives testers full access - source code, architecture, server logs. It’s thorough, but it’s also overkill for an MVP. You’re not a bank. You don’t need that level of detail yet.
- Gray box is the sweet spot. Testers get basic access - maybe a user account, some API keys, the public URL. That’s how real attackers operate after they’ve signed up. They’re not insiders, but they’re not total strangers either.
According to TechMagic’s 2025 benchmark study, 87% of startup security pros choose gray box testing for MVPs. Why? Because it’s fast, realistic, and focused. It finds the flaws that matter most: authentication breaks, API leaks, and privilege escalations. These are the exact things that get exploited in real attacks.
Gray box testing also fits your timeline. Most MVP tests take 2 to 5 business days. That’s less than a week. You can run it between sprints. You don’t need to pause development. You just need to schedule it.
The Five Steps of an MVP Penetration Test
A good penetration test isn’t just a scan. It’s a story. It follows a path a real attacker would take. Here’s how it usually plays out:
- Enumeration - The tester gathers info. What’s your domain? What APIs are exposed? What tools are you using? This is reconnaissance. No attacks yet. Just mapping.
- Vulnerability Assessment - They look for known weaknesses. Are you using outdated libraries? Is your server misconfigured? Tools like OWASP ZAP and Burp Suite Pro help here, but they’re just the start.
- Exploitation - Now they try to break in. Can they log in with a default password? Can they steal a session token? Can they access data they shouldn’t? This is where the real value happens.
- Post-Exploitation - Once inside, what can they do? Can they read customer emails? Delete records? Upload malware? This shows how bad things could get.
- Lateral Movement - Can they move from one system to another? From the web app to the database? From the database to your internal tools? This reveals how deeply your systems are connected - and how fragile that connection is.
This isn’t magic. It’s methodical. And it’s not about scaring you. It’s about showing you exactly where you’re vulnerable - and how to fix it.

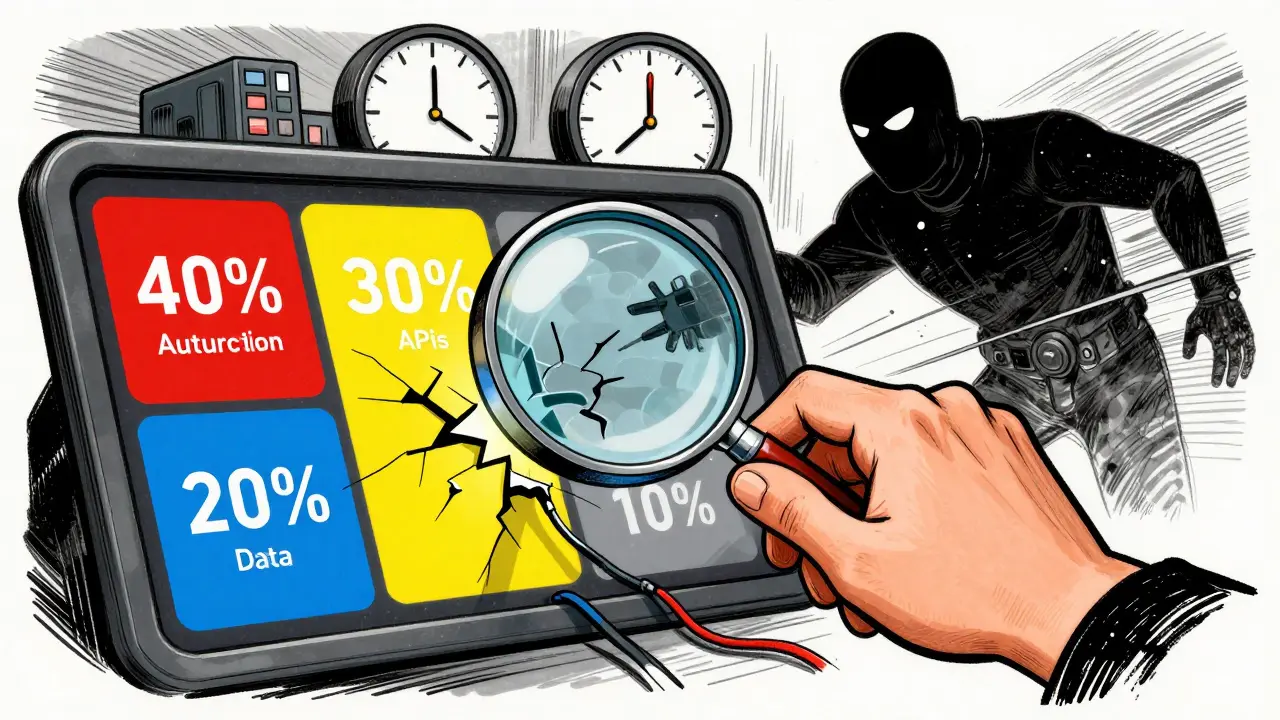
Where to Focus: The 40-30-20-10 Rule
You can’t test everything. And you shouldn’t try. The Cloud Security Alliance’s 2024 Startup Security Report gives you a simple breakdown:
- 40% on authentication - This is the front door. If attackers can log in as anyone, you’re already lost. Check for weak passwords, missing MFA, session hijacking, and brute force protections.
- 30% on API security - Your MVP likely runs on APIs. Are they properly authenticated? Do they return too much data? Are they rate-limited? A single unsecured API can leak your entire user base.
- 20% on data storage - Is your database encrypted? Are backups accessible? Are secrets stored in code? This is where breaches become disasters.
- 10% on network infrastructure - Firewalls, ports, server configurations. Less critical for early MVPs, but still worth checking.
Focus here, and you’ll catch 92% of critical vulnerabilities, according to GrSEE’s 2024 report. That’s not bad for a few days of work.
What It Costs - And What It Saves
Let’s talk money. A basic gray box test for a web app runs $1,500 to $5,000. That’s it. For a startup, that’s less than one developer’s week. Compare that to the $15,400 average cost of fixing a flaw after launch. Or the $250,000 in breach-related costs a single exposed API can cause.
Mark Chen, founder of a logistics SaaS tool, spent $2,800 on a gray box test before launch. They found 17 critical issues - including an admin API that let anyone download all customer records. He fixed them. Launched. And says it saved him an estimated $250,000.
That’s not an outlier. It’s the norm. Companies that test pre-launch fix issues 83% faster. They spend 68% less on remediation. And they avoid the worst thing of all: losing customer trust.
Some say, “We can’t afford it.” But the real question is: can you afford not to?
Tools and Teams: What You Need
You don’t need a team of 10 security experts. But you do need the right mix.
Automated tools like Burp Suite Pro ($399/month) or OWASP ZAP (free) are great for scanning. But they miss logic flaws. A human tester finds what software can’t. The best approach? Combine both. TechMagic found teams using automated tools + manual testing catch 32% more vulnerabilities than those using one alone.
When hiring a firm, look for experience with startups. Not big enterprise clients. Not banks. Startups. Ask for references. Ask how they handle scope creep. Ask if they provide a remediation playbook - a clear, step-by-step guide on how to fix each issue. Only 32% of providers do. But those that do see 53% higher fix rates.
And make sure your dev team is involved. The best tests happen when testers and developers talk. Weekly syncs. Shared dashboards. Joint review sessions. That cuts resolution time by 45%.
What Penetration Testing Can’t Do
It’s not a magic shield. It won’t catch everything.
It won’t find business logic flaws - like a pricing rule that lets users pay $0.01 for a $500 service. Those only show up when real users interact with the system. Only 12% of MVP tests catch these.
It won’t fix bad design. If your app was built without security in mind, testing will show you how broken it is. But you still have to rebuild.
And it won’t stop social engineering. If someone calls your support team pretending to be a founder and gets reset passwords, no penetration test will catch that. That’s training, not tech.
Penetration testing isn’t about perfection. It’s about reducing risk. It’s about saying, “We didn’t ignore the obvious.”
What Comes Next: Beyond the MVP
Don’t think of penetration testing as a one-time box to check. Think of it as a habit.
The Center for Internet Security recommends testing at three points: after MVP completion, after major feature updates, and quarterly after launch. That’s it. Three times a year. That’s manageable.
And the future is even better. AI tools are now cutting test times by 35%. Platforms like Apiiro are building Minimum Viable Security (MVS) frameworks that integrate testing directly into your CI/CD pipeline. That means testing happens every time you push code - not as a separate step.
By 2026, 72% of security leaders expect testing to be part of the build process, not a delay. The best startups aren’t waiting until launch to test. They’re testing every day.
Final Thought: Security Isn’t a Feature. It’s the Foundation.
Every startup wants to move fast. But speed without safety is just momentum toward disaster. Penetration testing isn’t slowing you down. It’s keeping you from crashing.
You don’t need to be a security expert. You just need to care enough to ask the right questions. Who tested this? What did they find? Did we fix it? Did we verify it?
If you’re launching an MVP this month, and you haven’t run a penetration test - stop. Schedule it. Pay for it. Do it before your first user signs up. Because the cost of waiting isn’t just financial. It’s emotional. It’s reputational. And sometimes, it’s irreversible.
The best time to secure your MVP was yesterday. The second best time is now.
Is penetration testing really necessary for a small MVP?
Yes - especially for small MVPs. Startups are targeted because they’re seen as easy to break into. A basic gray box penetration test costs $1,500-$5,000 but can prevent a breach that costs $100,000+ in recovery, legal fees, and lost trust. The Ponemon Institute confirms fixing issues pre-launch is 12x cheaper than after launch.
What’s the difference between vulnerability scanning and penetration testing?
Vulnerability scanning is automated - it looks for known weaknesses like outdated software. Penetration testing is manual and creative - it tries to exploit those weaknesses like a real attacker. OWASP’s 2025 benchmark shows penetration testing finds 4.7 times more critical flaws than scanning alone. Scanning is a checklist. Pen testing is a simulation.
Can I do penetration testing myself with free tools?
You can run scans with tools like OWASP ZAP, but you won’t find the real risks. Most critical vulnerabilities in MVPs - like broken authentication or API logic flaws - require human intuition. Automated tools miss 60% of these. For an MVP, it’s worth investing $2,000-$5,000 in a professional gray box test. The ROI is clear.
How long does an MVP penetration test take?
Most MVP tests take 2 to 5 business days. The process includes reconnaissance, exploitation, and reporting. Critical findings should be fixed within 14 days of the test. Many startups schedule testing right after their final sprint ends, so fixes can be included in the launch build.
What if my MVP is just a prototype with no users yet?
Even prototypes need testing if they’re connected to the internet. Attackers don’t wait for users. They scan for exposed APIs, misconfigured servers, and open ports. If your prototype has a public URL, it’s already visible. A quick 2-day test can prevent your prototype from becoming a headline.
Do investors care if I’ve done penetration testing?
Yes - and it’s becoming a requirement. 63% of Fortune 500 companies now demand penetration test reports from startups they partner with. Investors know that security flaws kill startups faster than lack of users. A clean test report signals maturity, reduces risk, and makes funding easier to secure.
What’s the most common vulnerability found in MVPs?
Exposed admin interfaces and unauthenticated APIs. In 2024, GrSEE found that over 60% of MVPs had at least one API endpoint that returned sensitive data without requiring login. These are often overlooked because they’re “internal” - but if they’re publicly accessible, they’re fair game for attackers.
Should I test my MVP before or after I get my first users?
Before. Always before. Once users are in, you’re responsible for their data. If you get breached before you’ve tested, you’re not just vulnerable - you’re negligent. Testing before launch gives you time to fix issues without putting users at risk. It’s not just smart. It’s ethical.
Susannah Greenwood
I'm a technical writer and AI content strategist based in Asheville, where I translate complex machine learning research into clear, useful stories for product teams and curious readers. I also consult on responsible AI guidelines and produce a weekly newsletter on practical AI workflows.
Popular Articles
6 Comments
Write a comment Cancel reply
About
EHGA is the Education Hub for Generative AI, offering clear guides, tutorials, and curated resources for learners and professionals. Explore ethical frameworks, governance insights, and best practices for responsible AI development and deployment. Stay updated with research summaries, tool reviews, and project-based learning paths. Build practical skills in prompt engineering, model evaluation, and MLOps for generative AI.







Wow. Just... wow. You actually wrote a whole essay about something that should be obvious. If you're launching an MVP and you haven't tested for security, you're not a founder-you're a liability. I've seen this so many times. The founders think they're being agile. They're just being reckless. $87k? That's cheap. I know one that lost $2M and their entire investor base because they skipped this. Stop pretending you're special. Test. Now.
gray box is the only way to go for mvp no cap. white box is overkill black box is too slow. i saw a startup last month get owned because they used a scanner and called it a day. bot found 3 vulns. real tester found 17 including an endpoint that returned all user emails with a GET request. no auth. no headers. just /api/users. like wow. how. also burp suite free works fine if you know what ur doing
I love how this post breaks it down so clearly-thank you for writing this. So many founders think security is for ‘big companies’ or ‘later’ and it’s just not true. I’ve mentored 12 early-stage startups this year and 9 of them had at least one critical API flaw they didn’t even know about. Gray box testing isn’t a cost-it’s insurance. And honestly? It’s empowering. When devs see a real exploit in action, they *get it*. They stop treating auth like an afterthought. And that cultural shift? Priceless. If you’re reading this and you’re about to launch-please, book that test. Your future self will hug you.
the 40-30-20-10 rule is spot on. authentication is the front door and so many startups leave it wide open. i had a client last week who had their admin panel on /admin and the password was admin123. no joke. and they thought they were safe because no one knew about it. lol. security isn't about hiding. it's about not being dumb. also yes test before users. period. end of story
Everyone’s acting like this is groundbreaking. Newsflash: if your app has a login, it’s hackable. If it has an API, it’s probably leaking data. If you’re launching without testing, you’re just asking to be the next headline. I’m not mad. I’m just disappointed. Again. This is the 4th time this month I’ve seen this exact mistake. Can we just… stop?
YES YES YES 💪 this is the kind of post that saves startups. Seriously. I’ve been on both sides-built the app, then got the breach email. Don’t wait. Do the test. Even if it’s just $1500. It’s the cheapest thing you’ll ever spend. And if you’re nervous about hiring someone? Find a freelance pentester on Upwork with startup reviews. I used one last quarter-5 days, $2200, fixed 14 issues. Now my investors ask for the report before every round. It’s not a cost. It’s a credibility booster. You got this 🙌